Mozilla Is Rolling Out Redirect Tracking Protection In Firefox In A Somewhat Concerning Fashion
The Mozilla Corporation included a new feature called "Enhanced Tracking Protection 2.0" when they released Firefox 79 but they did not enable it - until now. The new "enhanced" tracking protection blocks known redirect domains used by-pass third party cookie blocking and set cookies anyway. This is good news but they way they are rolling this new feature out is rather concerning. There may be a devil or two in the details.
written by 林慧 (Wai Lin) 2020-08-05 - last edited 2020-08-06. © CC BY
Mozilla Firefox 79 with the WJSN Happy Moment theme showing the hidden about:config preference configuration page.
Mozilla rolled out "Tracking Protection" with Firefox 67 in June 2019. They are now activating a new "Enhanced Tracking Protection 2.0" feature included, but not activated, in Firefox 79.
The Problem: The Advertisement Industry Is Seeking Alternative Solutions To Third Party Cookies[edit]
The smaller web advertisement companies are very displeased with third party cookies being phased out in all the major web browsers.
Many advertisement companies, and larger websites, have begun using special domains who do nothing but set a cookie and redirect users when they click on advertisements and other content of interest. It works like this: You visit website A and click a link on an advertisement. That link takes you to website B. Website B sets cookie and redirects you directly to website C. Website B gets to ask the web browser to set a first-party browser cookie and correlate your click to other clicks by you on other websites. This trick lets corporations track you even if you are using a web browser which a) blocks third party cookies and b) blocks the HTML ping attribute (<a href="https://linuxreviews.org/" ping="https://big-brother.is/recording-your-click">). Recent Firefox versions block third party cookies and Firefox never implemented the HTML ping attribute.
Redirect domains are mostly used by those who provide third party JavaScript to other websites. We can easily make a link to this domain redirect you somewhere else and log it and set relevant cookies. The Google search engine uses a onmousedown event to rewrite links you click on into tracking links that go through google.com. Twitter does use a redirect domain for tracking even though they could use twitter.com. That is why copy-pasting a link to https://somesite.tld/whatever from Twitter gives you a link like https://t.co/QV5PvilFg3?amp=1 instead of the actual link to the target website.
Mozilla Firefox 79+ will now provide protection against tracking using third party domains that are used for pure redirection purposes. This protection will only be applied to trackers on third party redirect domains. Blindly removing cookies created by first party redirects on sites like google.com is a bit problematic since it would potentially interfere with those sites' functionality.
There Are Devils Is In The Details[edit]
Mozilla included the new "Enhanced Tracking Protection 2.0" feature when they released Firefox 79 but they did not actually activate it. The code sat there, dormant, until Mozilla decided to remotely activate the new feature with no user input or interaction.
"Without needing to change a setting or preference, this new protection deletes cookies that use workarounds to track you so you can rest easy."
Latest Firefox rolls out Enhanced Tracking Protection 2.0; blocking redirect trackers by default
published August 4th, 2020
The setting Mozilla is remotely changing in this particular case is privacy.purge_trackers.enabled (You can type about:config into the address bar and search for it to see its status).
Mozilla has had the ability to remotely change your local Firefox settings and even stop Firefox from working for quite some time. The Firefox 67 release notes admitted that:
"Firefox will now protect you against running older versions of the browser which can lead to data corruption and stability issues"
It is fair to ask if a web browser vendor should have the ability to remotely activate or deactivate features, change settings and even prevent the web browser from being used with no end-user input.
Mozilla Decides, For Your Protection[edit]
The way the new "Enhanced Tracking Protection 2.0" is implemented is also potentially problematic. Firefox does not have code that will automatically detect if a domain is being used for pure redirection purposes or not. The tracking protection relies on blacklists and whitelists fetched from Mozilla on a regular basis.
"Once every 24 hours ETP 2.0 will completely clear out any cookies and site data stored by known trackers.
(..)
This only applies to known trackers; cookies from non-tracking sites are unaffected"
published August 4th, 2020
The actual list Mozilla uses is basing their "enhanced" tracking protection on is maintained by disconnect.me. That list is used as a base, they are not using it "as-is".
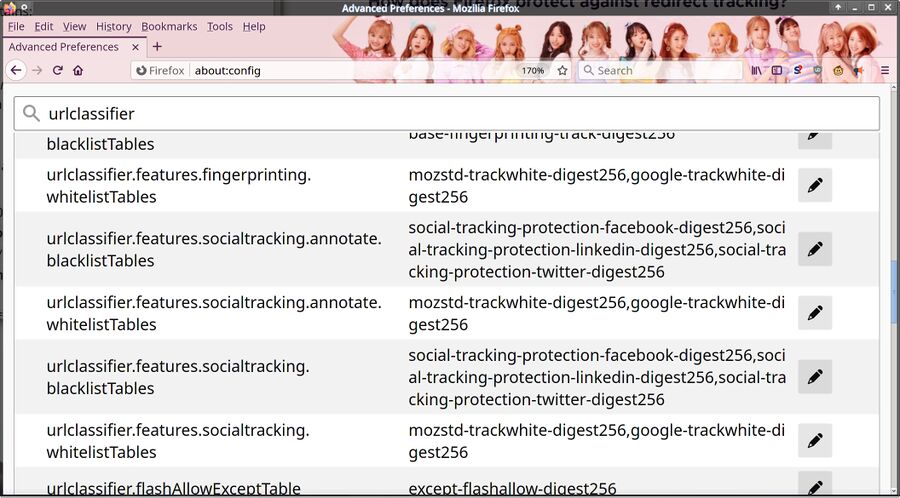
We are not entirely sure why urlclassifier.features.socialtracking.annotate.blacklistTables has:
- social-tracking-protection-facebook-digest256
- social-tracking-protection-linkedin-digest256
- social-tracking-protection-twitter-digest256
While urlclassifier.features.socialtracking.whitelistTables contains:
- mozstd-trackwhite-digest256
- google-trackwhite-digest256
Mozilla wouldn't be blocking tracking only from the large corporations they do not have deals with while at the same time allowing tracking the one very from large corporation they do have a deal with, would they?
Start By Cleaning Your Own Room[edit]
On a last little note, we would very much like to point out a whole lot of links that are hard-coded into Mozilla Firefox have UTM URL tracking codes embedded in them. Here are some examples:
app.normandy.shieldLearnMoreUrl:https://www.mozilla.org/%LOCALE%/firefox/%VERSION%/releasenotes/?utm_source=firefox-browser&utm_medium=firefox-browser&utm_campaign=whatsnew.browser.contentblocking.report.proxy_extension.url:https://fpn.firefox.com/browser?utm_source=firefox-desktop&utm_medium=referral&utm_campaign=about-protections&utm_content=about-protectionsbrowser.safebrowsing.provider.google.gethashURL:https://safebrowsing.google.com/safebrowsing/gethash?client=SAFEBROWSING_ID&appver=%MAJOR_VERSION%&pver=2.2
It is fair to ask why a supposedly privacy-focused web browser would take you to a link with tracking codes in it when you click ▸ ▸ .
It is nice that Mozilla is supposedly such concerned with your privacy and it is nice that they are rolling out enhanced protections against a very select narrow corporations they decide you need protection from. That does, of course, not include partners who are financing them.
It would be even nicer if Mozilla started by removing all the built-in tracking from their Firefox web browser product. Not exempting specific "partners" from their tracking "protection" would also be a welcome move. Mozilla does have a dwindling user-base and their revenue has been steadily declining for years, leading to Mozilla firing 70 employees in January, so those things may be too much to wish for. But one can hope.



Enable comment auto-refresher
Intgr
Permalink |
Jamiefoxx
Permalink |
Anonymous (8d3be43297)
Permalink |
Anonymous (93a438458e)
Permalink |