Remotely Exploitable Root Vulnerability In OpenSMTPD Disclosed
OpenSMTPD is a e-mail server developed as a part of OpenBSD. It is available for GNU/Linux and most other UNIX-like systems. Security researches at the cloud provider Qualys have found a serious gaping hole in OpenSMTPD which allows an attacker to gain root privileges by sending a carefully crafted e-mail message. You absolutely have to upgrade to OpenSMTPD version 6.6.2p1 if you or your organization is using it on your e-mail server.
written by Öyvind Sæther 2020-01-30 - last edited 2020-01-30. © CC BY
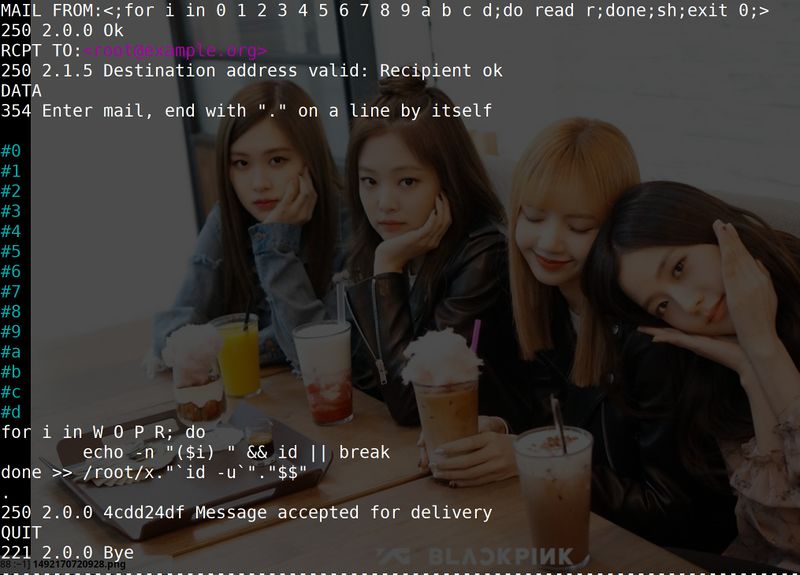
Proof of concept root exploit for OpenSMTPD. The terminals background features the k-pop group "Blackpink".
The cloud provider Qualys published several really beautiful root exploits for OpenBSD in December and they are still at it. Their latest proof of concept root exploit for OpenSMTPD is simple, elegant and just as beautiful as their previously published exploits.
Qualys found that the smtp_mailaddr() function responsible for validating sender and recipient mail addresses can be used to run shell code by sending a specially crafted e-mail message thanks to a logic issue which by-passes any sanity check in this function. The issue is assigned CVE number CVE-2020-7247.
The smtp_mailaddr() exploit is limited to shell code which is less than 64 characters. Qualys overcame that limitation in their sexy proof of concept by stuffing more shell code in the message body.
Qualys tested their proof of concept on OpenBSD 6.6 and Debian testing. The same exploit will work on any other UNIX-like system running OpenSMTPD. OpenSMTPD is developed as a part of OpenBSD but it is not limited to OpenBSD, packages for it are available in all the GNU/Linux distributions.
OpenSMTPD is not installed or started as a default on any GNU/Linux distribution but there are some administrators who have set it up on GNU/Linux machines. OpenSMTPD is installed by default on OpenBSD where it, by default, is configured to only accept mail from localhost. That means that local users and programs can exploit this in OpenBSDs default configuration. It is remotely exploitable on OpenBSD, GNU/Linux and other systems if it is configured as a general-purpose mail server listening on Internet-facing interfaces.
This is not a general SMTP issue, victims do need to run OpenSMTPD. Qmail, Postfix, Sendmail and other SMTP servers are not effected.
The OpenBSD team have written a patch fixing the hugely embarrassing vulnerability in smtp_mailaddr() and released a new version of OpenSMTPD. You absolutely have to upgrade to version 6.6.2p1 if you are running OpenSMTPD on a Internet facing server.
We fully expect Qualys to publish more exploits for OpenBSD maintained software in the near future. And we can't wait for them to take a very hard look at GNU/Linux distributions once they are done with OpenBSD.


Enable comment auto-refresher