GnuPG 2.3.0 Is Released With New Default Public Key Algorithms, A New Key Daemon And More
GnuPG is the standard for e-mail encryption and package signing within the FOSS world. Version 2.3.0 has a few notable improvements over previous versions. It has a new key database daemon for faster key look-ups, the default algorithms for new public keys is changed to ed25519/cv25519 and several of the tools, including gpg and the scdaemon smart card daemon, have quite a few new command-line options.
written by 윤채경 (Yoon Chae-kyung) 2021-04-11 - last edited 2021-04-11. © CC BY
A ASCII-armored public GnuPG key.
GnuPG is the de-facto standard for encrypted e-mail, and to some degree encrypted instant messages, within the free software world. Most FOSS e-mail software has built-in support or plugins for it. It is also used to sign software releases, ISO images for GNU/Linux distributions and a whole lot more. Nobody outside the FOSS community uses it or cares about it, which is a bit sad.
GnuPG 2.3.0 has quite a few improvements over previous versions. It now comes with a still experimental key database daemon that uses a SQLite database to store the keys. It can be enabled by adding use-keyboxd to $HOME/.gnupg/gpg.conf. There is a new separate configuration file for it called $HOME/.gnupg/gpgsm.conf. This daemon makes key look-ups much faster.
There's also a new tpm2d daemon for physically binding keys to a machine. You can read more about it in a blog post on gnupg.org titled Using a TPM with GnuPG 2.3. Most newer laptops in the upper price range come with a TPM module. Desktop computers tend to come with a empty motherboard header where one can be installed, so this is mostly useful if you have a fairly new high-end laptop or you are willing to buy a TPM module.
New GnuPG keys are now, by default, created with the ed25519/cv25519 public key algorithms. Similarly, AES is now the new last resort cipher preference instead of 3DES.
Support for AEAD encryption using OCB or EAX, v5 key signatures and X448 curve (ed448, cv448) encryption has been implemented in this release.
The release notes mention that there is a "New option --chuid for gpg, gpgsm, gpgconf, gpg-card, and gpg-connect-agent". gpg --help lists no such option so you would have to refer to the updated manual page to learn that it can:
"Change the current user to uid which may either be a number or a name. This can be used from the root account to run gpg for another user. If uid is not the current UID a standard PATH is set and the envvar GNUPGHOME is unset."
GnuPG 2.3.0 has several new command-line options: --full-timestrings to print date and time, --force-sign-key to force the generation of a key signature even if one already exists and --no-auto-trust-new-key to not set the owner trust of new keys to "ultimate". None of those have been added to the output of gpg --help to ensure that nobody will find out about them, or what they do, unless they read the gpg.1 manual page.
The scdaemon Smartcard daemon that comes with GnuPG has gained two new command line options:
--application-priority, "change the application priority to LIST"--pcsc-shared, "use NAME as PC/SC driver"
Both of those will actually show up if you run ./scd/scdaemon --help. The scdaemon.1 manual page has more details.
Compiling and installing GnuPG 2.3.0 may be a tiny bit problematic. It requires the libassuan library, available from https://gnupg.org/ftp/gcrypt/libassuan/, to compile. libassuan comes with a header file named assuan.h in the folder /usr/include/libassuan2/. GnuPG 2.3.0 likes to complain that:
kbx-client-util.c:27:10: fatal error: assuan.h: No such file or directory
..even if you have /usr/include/libassuan2/assuan.h in place.
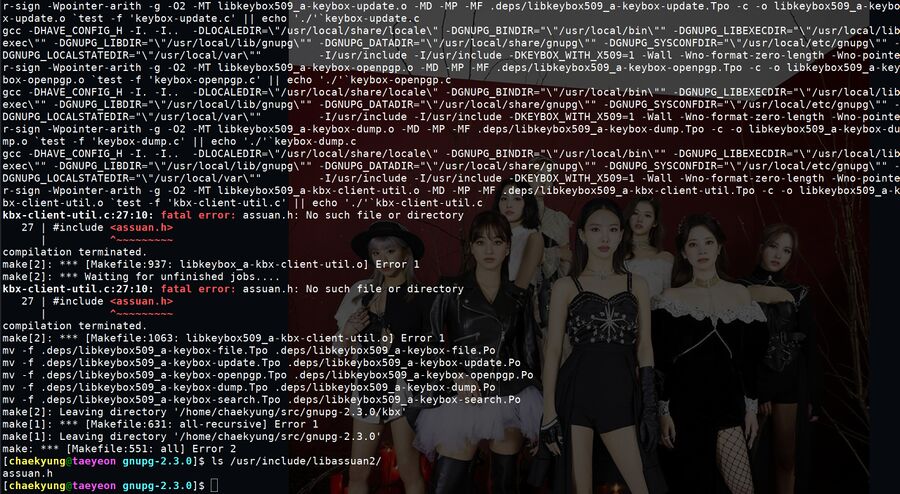
A GnuPG 2.3.0 compile failure.
You can "fix" that idiocy about a missing assuan.h with a ln -s /usr/include/libassuan2/assuan.h /usr/include/assuan.h and make it happily compile as along as you have the libassuan headers and the libksba headers installed.
You can acquire the source code for GnuPG 2.3.0 from https://gnupg.org/ftp/gcrypt/gnupg/ or one of the mirrors if you prefer a local source. gnupg-2.3.0.tar.bz2 is just 7.3 MiB, it is not a huge download where it makes any difference where you get it as long as it's not a compromised version. You can check if it is with gpg --verify gnupg-2.3.0.tar.bz2.sig gnupg-2.3.0.tar.bz2 or, if you don't already have GnuPG, sha1sum gnupg-2.3.0.tar.bz2. It's supposed to be 44d06ef6625378e2d135420543e5fb06b62437ab.
The GnuPG homepage is at https://gnupg.org/ and the full 2.3.0 release-announcement can be read on the gnupg-announce mailing list (https://lists.gnupg.org/pipermail/gnupg-announce/2021q2/000458.html).


Enable comment auto-refresher