ClamAV 0.103.2 Is Released With Security Fixes For Four Vulnerabilities
The free software anti-virus package ClamAV has, ironically, made a security release fixing four vulnerabilities in the ClamAV scanner. Two of them could cause it to crash, one could cause it to enter a endless loop and a Windows-specific vulnerability could lead to privilege escalation. You should update if you use ClamAV as a part of a production mail server setup. ClamAV has 8,532,858 virus signatures it can scan for in its database.
written by 윤채경 (Yoon Chae-kyung) 2021-04-10 - last edited 2021-04-10. © CC BY
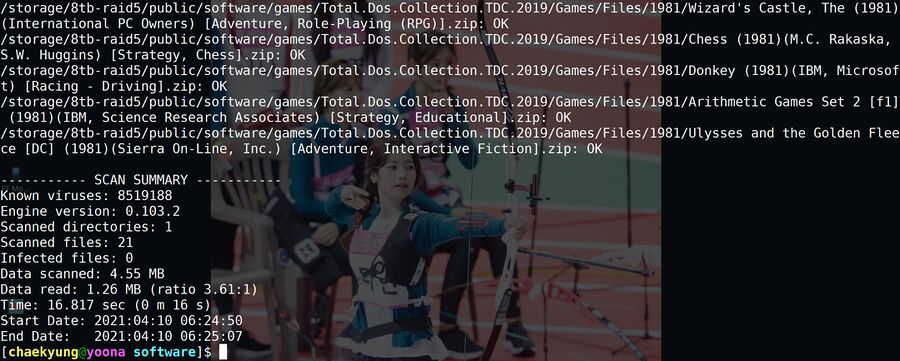
ClamAV reporting that it did not find any virus.
It is somewhat ironic that the anti-virus and security scanner ClamAV has just made a security release fixing four different vulnerabilities in ClamAV:
- CVE-2021-1404, a vulnerability caused by improper variable initialization which would could lead to a NULL pointer read and a subsequent ClamAV crash if ClamAV encountered a specially crafted file.
- CVE-2021-1405, a vulnerability in the PDF parsing module that would make ClamAV crash if it encountered a specially crafted PDF file. ClamAV didn't properly keep track of the buffer size it used. That would result in a heap buffer over-read if it encountered a specially crafted PDF file.CVE-2021-1404z
- CVE-2021-1252, a vulnerability that would cause ClamAV to loop forever if it encountered a specially crafted Excel .XLM file.
- CVE-2021-1386, a Windows-only vulnerability which differs from previously mentioned issues. Previous ClamAV versions would load the UnRAR DLL in a unsafe way which opened the door for local user privilege escalation by replacing the UnRAR DLL with a malicious file.
The first three of these vulnerabilities should not be brushed off as being insignificant, and that is specially true if you are deploying ClamAV as a part of your mail-server setup. It would only be a simple matter of sending you a maliciously crafted e-mail.. or thousands, if you use a setup where a new ClamAV processes is spawned for individual e-mails. An avalanche of malicious .XLM files could spawn enough ClamAV instances stuck in endless loops to cause noticeable problems.
There's also a fix for a memory leak in the PNG parsing code and a ClamOnAcc scan on file-creation race condition in ClamAV 0.103.2. ClamOnAcc, clamav on on-access, is a real-time anti-virus scanner you can deploy if you want to make your GNU/Linux machine as slow as a typical Windows machine by scanning every file you access or open in real time.
FreshClam, the tool for updating the ClamAV virus database on a regular basis, has also been improved. It handles fetch redirects and errors (HTTP 304, 403 and 429) better.
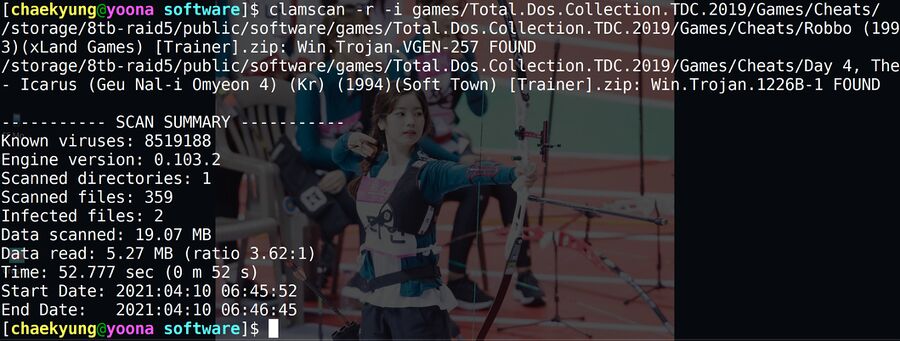
clamscan -r -i reporting that it found two viruses lurking in a folder full of cheats for old MS-DOS games.
ClamAV is completely free, and it can be quite handy even if you aren't administering the mail setup for some large corporation. It has been around since forever so it has all the signatures for viruses that are commonly distributed in not entirely legal "abandonware" packages with old MS-DOS games and Windows games. It can scan inside most file archives and identify viruses in all the file types they are able to hide in.
The complete ClamAV 0.103.2 announcement can be read at https://blog.clamav.net/2021/04/clamav-01032-security-patch-release.html. The homepage is at https://www.clamav.net/ (don't try https://clamav.net/, it doesn't work) and the latest version can be acquired from https://www.clamav.net/downloads.
ClamAV is available for GNU/Linux, BSD, Windows and macOS.
All the GNU/Linux distributions have ClamAV in their repositories, though some may not have the latest 0.103.2 version for a few days or even weeks in some cases.


Enable comment auto-refresher