Red Hat Recommends Disabling Hardware Acceleration on Intel Integrated Graphics Due To Hardware Flaw
Red Hat has issued guidance for the latest Intel CPU hardware bug which, unlike Meltdown and other widely publicized hardware flaws in Intel CPU products, affects the GPU part of Intel chips (if they have one). The proposed "solution" is a bit dramatic: just disable hardware acceleration and you'll be fine - unless you would like to watch videos or play games or do anything else in a graphical environment for that matter.
written by 윤채경 (Yoon Chae-kyung) 2020-01-17 - last edited 2020-01-22. © CC BY
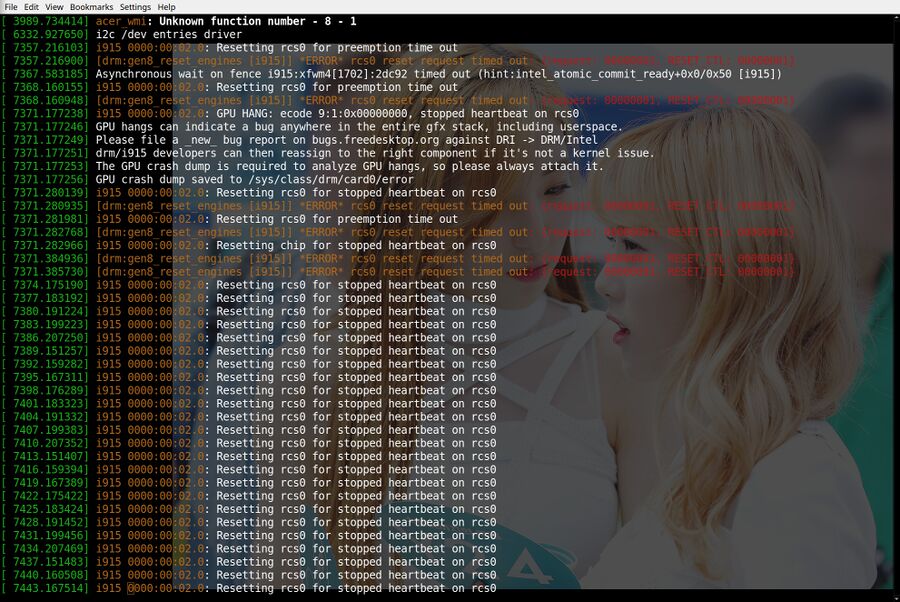
"[drm:gen8_reset_engines [i915]] *ERROR* rcs0 reset request timed out: {request: 00000001, RESET_CTL: 00000001}": The i915 kernel driver for Intel iGPUs is really buggy. Perhaps disabling it altogether isn't a too stupid idea?
The graphics part of Intel processors with integrated graphics have had a hardware flaw since Ivy Bridge where execution units (EU) used by one process can be re-used and accessed by another process. Recently released kernels have a workaround for gen9 Intel GPUs (Skylake to Comet Lake) which involves clearing the EU/L3 state on each context switch. That workaround has been applied to gen8 hardware ("Broadwell" up to but not including "Skylake") since 2017 for entirely different reasons. Older gen7/7.5 processors are also affected. Those chips remain vulnerable. The kernel code used by those chips is very different from the code used for gen8 and newer which means that any fix for gen7/7.5 hardware in future kernels can not and therefore will not be back-ported to stable branch kernels used by many GNU/Linux distributions.
Red Hat has issued guidance for the hardware flaw in integrated Intel graphics known as CVE-2019-14615 in the CVE database and PSIRT-TA-201910-001 in Intel's ID system. Their recommended "mitigation" is:
"Preventing loading of the i915 kernel module will prevent attackers from using this exploit against the system; however, the power management functionality of the card will be disabled and the system may draw additional power"
They go on to casually mention a minor disadvantage to their recommended course of action:
"Graphical displays may also be at low resolution or not work correctly. This mitigation may not be suitable if the graphical login functionality is required."
Recently released kernels 5.4.12, 4.19.96, 4.14.165, 4.9.210 and 4.4.210 have a patch for gen9 Intel hardware. gen8 has had a workaround since 2017. It would therefore only make sense to blacklist the i915 kernel module on systems with the older Ivy Bridge (gen7) and Haswell (gen7.5) chips. Doing so would, practically speaking, be a huge disadvantage for everyone using the integrated graphics part of those processors.
Basic features like modern display resolutions, hardware accelerated graphics, OpenGL, Vulkan, hardware accelerated video playback and most other things you likely want to do on a desktop or laptop computer will not work on systems with integrated Intel graphics without the i915 kernel module. Display resolutions would be limited to low-resolution VESA standards without the kernel modesetting provided by the i915 module.
Red Hat's recommendation could make some sense on servers. A vulnerability which allows one process to get information from the graphical output of another is typically not a huge concern on servers since they do not tend to have any graphical programs running. Disabling the i915 kernel module for Intel graphics will therefore make little practical difference. One might want to do it anyway given that there is no downside to not having hardware accelerated graphics on a server. That is not true when it comes to laptops and desktops.
Desktop and laptop users with newer Intel processors with integrated Intel graphics should ignore Red Hat's advice and, instead, make sure they are using an updated kernel. That will not help those with Ivy Bridge / Haswell hardware, the only current solution for those chips is to follow Red Hat's recommendation and disable the i915 kernel module. That makes the iGPU practically unusable so it is probably not something you want to do even if it does leave a gaping security hole open for exploitation. That may be a risk worth taking given that this is not a remotely exploitable vulnerability, it is only a problem if you have malicious software running on your machine. How much risk you are willing to take is a very personal choice. Choose wisely.


Enable comment auto-refresher