Tor Snowflake launched as a censorship countermeasure for the The Onion Router network
The Onion Router's many nodes are banned by quite a few tyrannical regimes around the world. Tor has a feature called "bridges" which helps by-pass local censorship. Bridges are computers who act as middle-men between end-users and the Tor network. They are not listed in the Tor directory and they are meant to be hard to learn. It is, of course, possible to pretend you are a lots and lots of end-users in order to learn all the bridges. Tor's new "Snowflake" browser-plugin aims so make Tor even more censorship-resistant by allowing anyone with that browser plugin to act as a proxy for Tor's bridges.
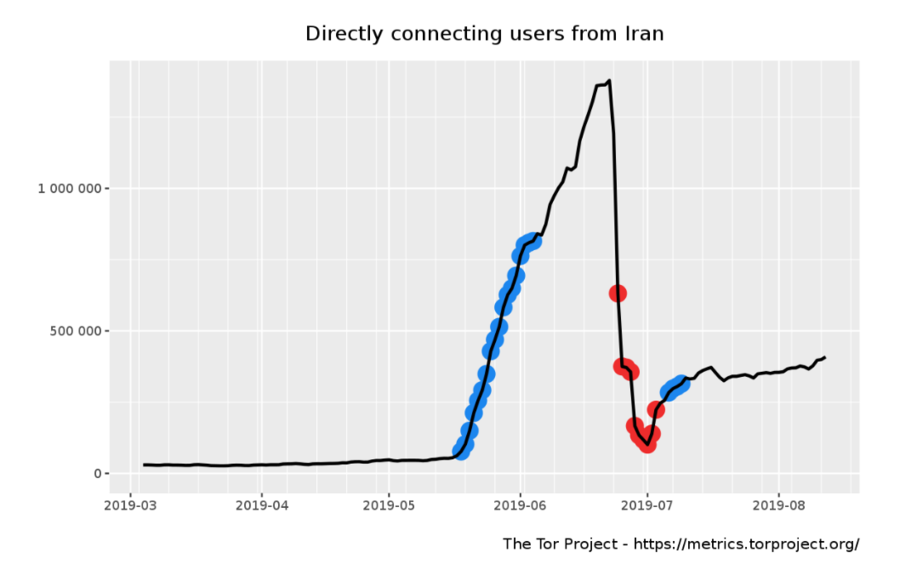
The amount of Tor users appeared to explode in Iran early June this year. Then the amount of "new users" dropped off a cliff.
We can only speculate if the explosion of supposed Tor users and the subsequent rapid decline in Iran had anything to do with learning all the Tor networks bridges or not (the graph appears to have leveled off at a higher base-line than it used to have). It is fair to say that making a lot of connections would be one way to learn all the Tor network's bridges in order to block them and prevent access to the Tor network.
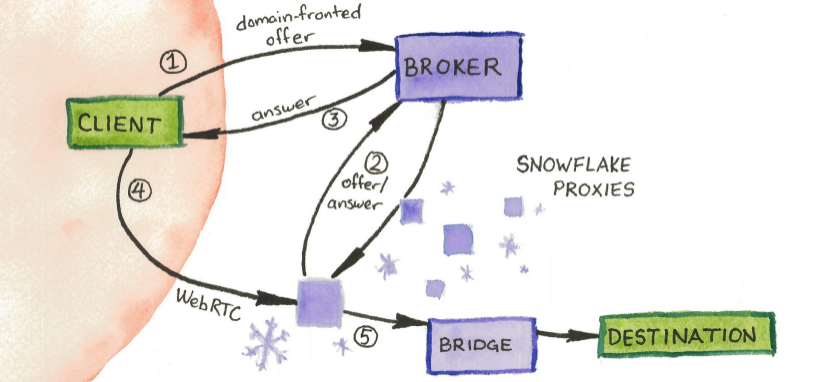
The Tor Project has now launched a new initiative called "Snowflake" which aims to make censoring the Tor network even harder. It works like this: People running a web browser in parts of the world where there is no Internet censorship can install a plug-in called "Snowflake". People in parts of the world where there is Internet censorship can connect to users running the "Snowflake" plugin and access the Tor network via that user and a bridge.
The "Snowflake" plug-in does not make your browser a regular proxy. Users who connect to the Internet via that plugin connect to Someone's Web browser with the Snowflake plug-in -> Tor bridge -> The Tor Network -> A Tor Exit Node. It will not be your IP listed in the logs of whatever web services those using your Snowflake proxy access, it will be the IP of the Tor exit node they happen to route through.
There are web browser plugins for Chrome and Firefox available at snowflake.torproject.org if you would like to help users in parts of the world with heavily censored Internet connections by-pass that censorship.
As for the security and anonymity aspects of using the Tor Network.. There are some hard questions one want to ask about the current state of this network. We'll leave you with the following snap-shot of the Tor network for your consideration:
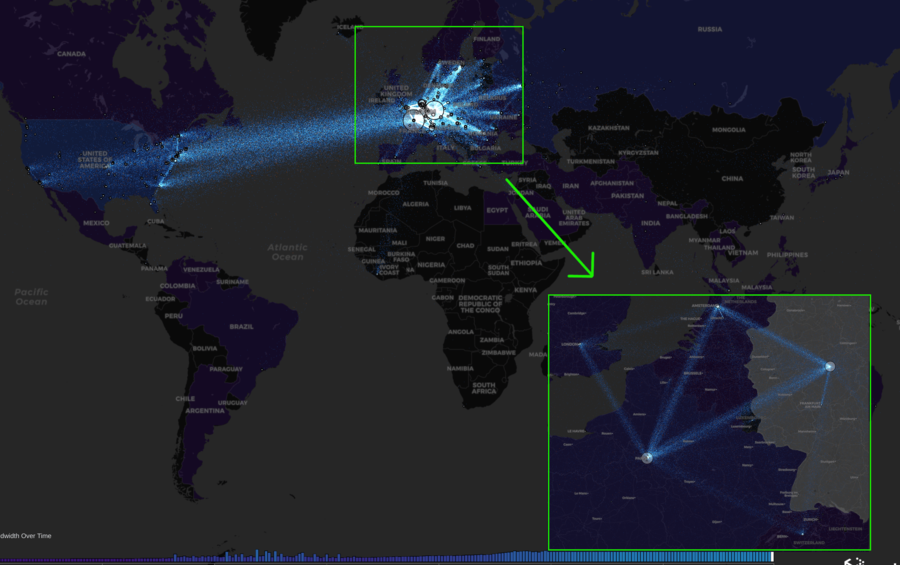
The Tor Network has thousands of nodes. That simple fact may make it sound like you're activities on the Tor network is untraceable but in reality the vast majority of Tor nodes are located in just four cities in Europe. Is it logical to conclude that it's pure chance that there's more "regular people" in four cities in Europe running Tor nodes than the rest of the world put together? Or could it be that there's something else going? Just asking.

Enable comment auto-refresher
Anonymous (ac4127566d)
Permalink |