The Nightly Tor Browser Build Has Support For Namecoin Domain Names
Location hidden services accessible on the Tor network have been using very unmemorable base32-encoded names since their inception. Remembering a domain name like kxzxnzfqkig53zcxmb45xkjeultr3rydxsg6763ybt7bq2nvpgy2ihyd.onion is not easy and nobody wants to type that into a web browsers address bar even if they somehow manage to memorize the address. The nightly version of the Tor Browser supports Namecoin domain names which work like and look like regular domain names from a end-user perspective. Moving from long random-looking domain names into shorter and more memorable domain names like federalistpapers.bit would make location hidden Tor services a lot easier to use.
written by 林慧 (Wai Lin) 2020-02-27 - last edited 2020-03-07. © CC BY
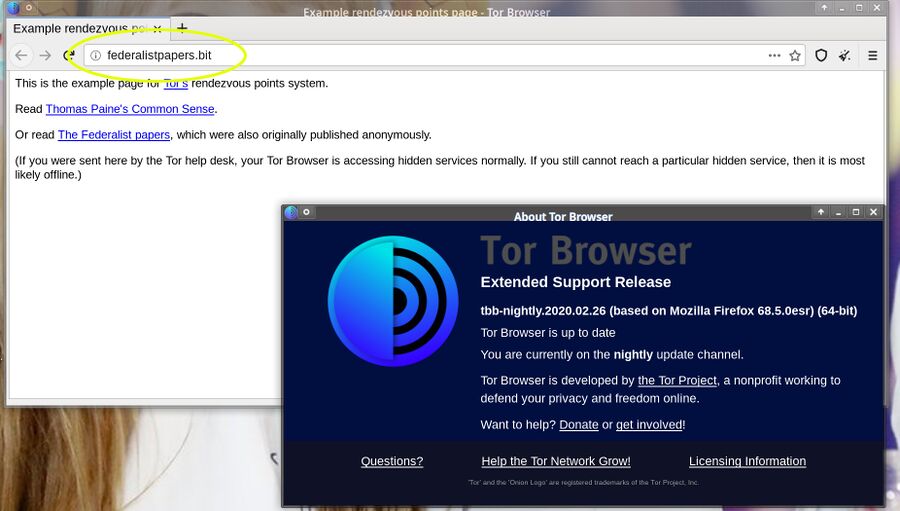
The nightly Tor Browser showing a namecoin domain.
The concept of mapping Namecoin domain names to Tor hidden service names is not new. Several experimental implementations have been around since 2011. Those were far from perfect. Performance has been a key issue. Tor hidden services are slow, adding a 5 minute DNS lookup delay before the Tor circuits are initialized would be bad.
The Nightly Tor Browser build has a new Namecoin implementation based on the light-weight Electrum-NMC Namecoin client. The Electrum-NMC version included in the nightly Tor Browser build is a stripped down and highly optimized fork which lacks most of the features that are not strictly required to securely map Namecoin .bit addresses to Tor .onion addresses. The total size of the new Namecoin functionality is just 3.3 MiB.
There is one minor problem with the current Namecoin implementation in the nightly Tor Browser builds: It is only available in the nightly GNU/Linux build. It is not available in the nightly Windows, Android or macOS builds and it is also not available in the "alpha" versions available on the Tor project's website. And is disabled by default. Those who want to try it can grab a nightly GNU/Linux build enable the Namecoin name resolution by setting the environmental variable TOR_ENABLE_NAMECOIN=1. Do note that you need to use the nightly Tor Browser build from f4amtbsowhix7rrf.onion/tor-browser-builds/ which is, for some odd reason, only available on that .onion address. That .onion address is listed on the trac.torproject.org "Hacking" page as well as the namecoin Tor Workshop page so you can use those to verify that it is genuine.
There are a few Tor-mapped Namecoin domain names available for those who want to test this feature. federalistpapers.bit, riseuptools.bit, submit.theintercept.bit and submit.wikileaks.bit will all work if you are using the nightly Tor Browser for GNU/Linux.
Those who want to setup their own hidden Tor service with a namecoin domain name should be very aware that owner anonymity was not a consideration in the current implementation. User anonymity was considered and prioritized. Those who utilize Tor to host not entirely legal services may want to forgo using namecoin domain names for now.
The namecoin domain name support is considered experimental at this stage. It is not clear if there will be support for it in the Nightly Tor Browser builds for Windows and macOS any time soon. Easy to use domain names like riseuptools.bit could be the standard way of accessing location hidden Tor services one year from now. It is also possible that this experimental support in the nightly Tor Browser version for GNU/Linux will amount to absolutely nothing.
Developer Jeremy Rand held a presentation about the Electrum-NMC implementation in the GNU/Linux version of the nightly Tor Browser at the 36th Chaos Communication Congress. There are slides and a video available for those who want to dive into the technical details.


Enable comment auto-refresher