OpenPGP keys are being spammed to the point where GnuPG is "useless"
The GNU Privacy Guard has been a standard way of encryption communications in the free software world for two decades. It never got any mainstream appeal and most people have never heard about it. That does not mean it's irrelevant, much of the free software infrastructure and many free software developers rely on it. It appears that someone has decided to make life rather difficult for certain GNuPG-using developers by spamming their keys with lots and lots of signatures. You may want to avoid updating keys from public key-servers if you rely upon GnuPG/OpenPGP.
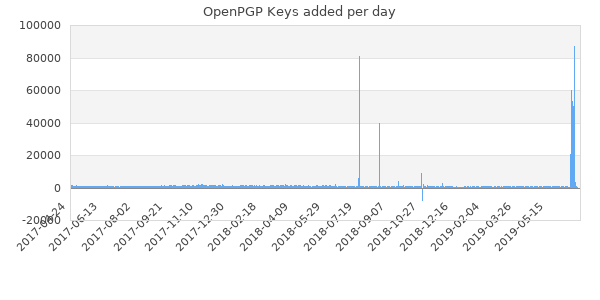
The above chart taken from sks-keyservers.net's status page indicates that something odd is going on. It would appear that someone has generated a lot of keys and submitted them to the public key-servers.
This would only be a problem for those operating public key-servers if they had stopped there. A lot of those new keys are being used to sign certificates belonging to public figures. This is a problem because a request to a key-server for my certificate will include all the signatures from people who signed it and it turns out that both GnuPG itself and a lot of software which uses it does not handle thousands of signatures.
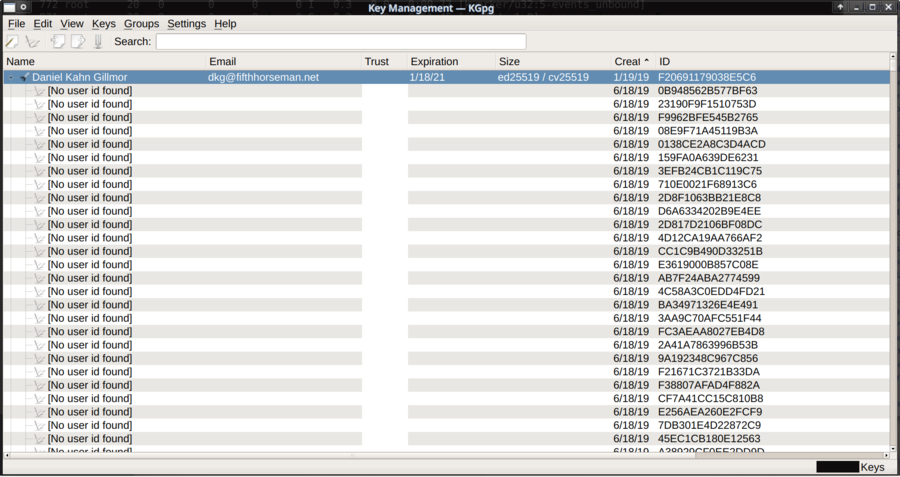
Debian-developer Daniel Kahn Gillmor reports that his personal public key is now 17 MB in a blog post dated July 28th, 2019. This, in his own words, makes it "unusable in standard workflows". We decided to try this challenge by importing his key from a public key-server - even though his blog-post specifically warns against doing just that. gpg struggled, running at 100% load on one CPU core, 20 minutes before it managed to import the key due to the unusually high amount of signatures attached to it.
His key is, indeed, pretty unusable. The attack on him may of course be personal. He did write the ietf draft "Abuse-Resistant OpenPGP Keystores" which describes and addresses this exact problem. However, he is not the only one hit with a flood of unwanted certificate signatures, there are other victims.
The implications are, in our opinion, pretty bad. There could be some rather important core parts of a modern Linux-based system that are reliant upon GnuPG functioning properly. Personal keys being spammed is actually not our biggest concern. The implications of spamming certain keys used by software projects could case more serious problems.
There are some open bugs dealing with this issue. Perhaps a solution will be found. Until then: Be careful what key-servers use and which keys you grab.

Enable comment auto-refresher