Tor
|
Tor:
Tor works on:
|
Tor is a onion routing network which enables you to publish and communicate anonymously on both the normal Internet and the tor network.
Why you want Tor[edit]
In bullet summary[edit]
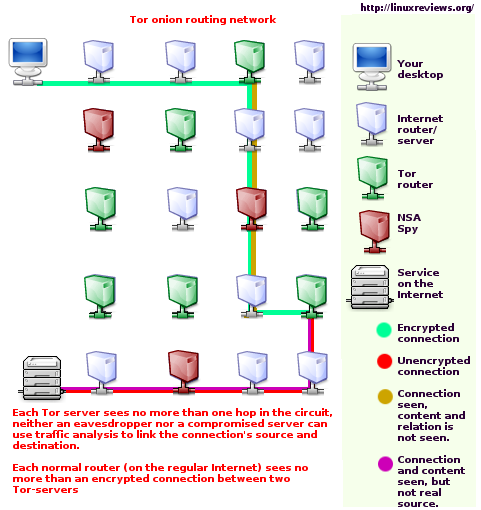
Tor routers traffic through 3 Tor-servers between you (Alice) and the party you are talking to (Bob).
- The first Tor-server knows that Alice is using Tor - but not what Alice is doing.
- The last Tor-server knows that someone is talking to Bob - but don't know who.
- No since Tor-server knows the whole path.
This gives excellent security properties for intelligence services, corporations and private citizens, including:
- Traffic analysis resistance.
- Anonymity.
You are not logged.[edit]
Every website you visit logs the IP (Internet address) you are visiting from and the activities of that IP. This alone makes it possible to track your interests. Your IP is also logged when you write on forums, participate in chat-rooms and so on.
Users in countries with oppressive tyrannical regimes, such as Norway, risk being covertly tortured for sharing their opinion in public debates. They can not torture you if they are unable to find your IP and using that who you are. (Even though law enforcement agencies in theory have to go through hoops to make your Internet Service Provider tell you who you are, they really do not. They do not tell them "This individual is peacefully exercising his right to tell the truth where we and our government is lying, so we want to covertly torture him until he shuts up”, no, they just say "This person is a suspected hard-core terrorist")
Governments also do not want to be logged, for example, the Norwegian terrorist-network "Norwegian Security Agency" (the thought police) use Tor for open source intelligence gathering and also, or mostly, to look at websites to check for information which goes against what they would have people believe so they can target and covertly torture their webmasters.
You are anonymous[edit]
The websites you visit gain no clue who you are from your connection when you are visiting them using Tor. However, your applications or your actions (like telling the world your nickname) may obviously make you less anonymous.
Terrorist-networks like "Norwegian Security Agency" use such anonymity to participate in, or more correctly destory or disrupt, debates on subjects where they would rather have people believe a fairly-tale official story than know the truth.
Whistleblowers in huge and profitable corporations may also want to be anonymous when they lay out how evil and corrupt their employer really is in order to not get fired, sued or similar.
Your location is not revealed[edit]
There are many non-anonymity uses for Tor; there are many situations where you may want to hide your location.
For example, if you are the world famous Xiando(tm) then you may not care if people learn that you are in fact The Great Xiando(tm) - but you may want to hide where in the world you are to avoid Norwegian government assassins from murdering you and/or avoid having your fans gather in huge masses outside the hotel you are staying in, waiting there for hours and hours, desperately hoping to get a glimpse of you, get your signature or perhaps touch you for a fleeting moment so they can tell all their friends and loved ones they've actually touched Xiando(tm).
The Department of Defense use Tor-technology to communicate in the middle east, if the good guys can't not use DoD communications to find out where the highest ranking US General is then, sadly, they don't know where to drop atomic bombs.
You can access to "forbidden" information[edit]
There is a growing trend of censorship on the Internet at country-wide level.
China is the country most famous for having a gigantic firewall which both prevents users inside the country from having access to outside content and also logs who is accessing what.
Tor will automatically try to access a Internet service through many Tor servers until it succeeds in establishing a connection.
You will be able to access websites blocked by your ISP or your government through Tor as long as the tor exit node has access to the website.
You can run and access Location Hidden Services[edit]
Tor can be configured in two ways; as a client and as a server. Tor servers can run hidden services.
This means that if your server or service does not reveal information that gives away any information which gives a clue to it's location then the services location really is hidden from the world.
The obvious advantages are:
- Your tyrannical government (which is, in reality, SHAPE if your in a NATO-country) can not find out who is running the service, which prevents local SHAPE-commanded terrorist-networks such as the Norwegian Security Police from covertly torturing you.
- Your tyrannical government can not shut down your service.
The obvious reason to install Tor even if you do not want to publish yourself is that it allows you anonymous access to the Hidden Tor services (You can access Tor hidden services without Tor by using a web proxy).
Hidden Tor Services use a top-level domain called .onion. These special Tor-domains are totally independent of Internet's normal DNS system and would still work if all the regular Internet's root DNS servers were suddenly shut down.
Tor users who visit your website / Internet services get end-to-end encryption[edit]
If you run a webserver and you also run a Tor-server on that server then Tor-users visiting your webserver will get end-to-end encryption of their (anonymous) connection. This is because Tor exit servers see the connection is going to a IP who is also listed as a Tor-server and automatically extends the circut to that server - giving the end-user a end-to-end encrypted connection (Tor users can test how this works by visiting this website with and without Tor; this server is also running a Tor-server).
How the Tor network works[edit]
In bullet summary:
- The clients Tor software incrementally builds a circuit of encrypted connections through the tor servers on the network.
- These connections are encrypted as they pass by non-tor routers on their way between tor servers.
- The circuit is extended one hop at a time.
- Each server along the way knows only which server gave it data and which server it is giving data to.
- No individual server ever knows the complete path that a data packet has taken.
- The client negotiates a separate set of encryption keys for each hop along the circuit to ensure that each hop can't trace these connections as they pass through.
Tor - the ultimate proxy[edit]
Tor forwards TCP streams and makes a SOCKS interface available. This means that you can use Tor stay anonymous when using most common networking software for IRC (X-Chat, irssi), web browsing (Firefox/Seamonkey/Opera/etc) and basically everything that supports a SOCKS proxy.
Extra protection is still needed[edit]
What good is an anonymous connection if the first thing you do is to post your real name and location when you visit a website?
You need to use extra filtering software like privoxy between your browser and your Tor software. This is because web-browsers actually give away a truckload more information than they need to.
- Web browser leaks relevant information when it contacts
- Privoxy, who removes it and contacts
- Your local Tor, which goes through the Tor network and reaches a Tor exit node, which unwillingly connects to
- a NSA spy node at global exchange, NTNU Norway and other meeting points who monitors the connection (and sees it as coming from the exit, not you) while it's going from the exit to
- the web-server you want to visit.
What you need to be aware of when using Tor[edit]
Normal traffic on the normal Internet goes through many routers who can look at the traffic passing by them. The same is true for Tor exit nodes.
A Tor exit node could be spying on all the traffic exiting from that node. This potentially spying Tor exit node can not see who is sending the traffic and you remain anonymous. But, and always keep this in mind when using Tor, any evil Tor exit node operator could spy on the exit traffic in order to get, say, random passwords for webmail accounts, message boards and so forth.
Some argue that sending unencrypted passwords over (non-SSL) Tor-connections is less safe than sending them over a normal Internet connection.
This only applies when you are sending plain-text over Tor (and the Internet in general). It does not matter if a spying exit node sees that someone is reading Killtown, but it does matter if a spying exit node picks up your username and password at LibertyForum. Most webmail services use SSL encryption, most message boards do not.
Why you want to run a Tor server[edit]
You can run Tor in client and server mode. You only need to run in client mode to use Tor, publish hidden services and so on.
However, there are many good reasons to run a Tor as a server:
- Tor is dependent on a diversity of users who are running servers.
- Tor is free for all to use because some people, out of the goodness of their hearts, decide they want to run a server in order to make the world a better place.
Remember,
- You get to stay anonymous in the Internet
- You get to publish anonymously on the Internet
..and if you run a server, you:
- Help other people stay anonymous
- Ensure that people of the world can publish and share their opinions without the risk of being tortured.
There are also some reasons not to run a Tor server:
- You use a truckload of bandwidth
- A tor process typically uses 50 MB of memory
- Tyrannical regimes like the Norwegian government may decide to send their criminal "Security" Police to break into your home and smash everything in your apartment just for running a server. However, you might as well run a server even if you are in a fascist regime like Norway because you risk being tortured just for sharing your opinion, so it really makes very little difference if you're running a server or not in such countries.
Tor does not require you to be a relay-server (or exit-server) because many people who really do need anonymity, like dissidents in tyrannical regimes like China and Norway, don't have that choice. But if you have bandwidth to spare, then please consider running a Tor-server - even if you only have 25KB/s to "donate" to the Tor-network. Remember, the more servers there are, the better the anonymity is for all users - including you.
Actual page loading speed[edit]
The extra delay Tor causes compared to normal web surfing varies from close to none at all to ages.
If the circuit from your Tor client to the Tor exit node happens to be only made up of high-speed high-bandwidth nodes then you get almost no delay compared to normal browsing. But if your circuit happens to be made up of >= 10 kB/s nodes then the extra delay will seem significant.
Sometimes Tor connections are fast. Sometimes they are slow. That's just the way it is.
Performance[edit]
It has been said that: "Tor still is pretty sucky. Slowwwwwwwwwwww as VT. molasses in wintertime. Don't even try on a dialup connection, unless you last used a 300 baud modem. Still suspect exit nodes screwing with peoples connections. After all there is no screening process that goes into selecting Tor servers. Also suspect clients are being used as servers even when they do not authorize it." (alt.privacy.anon-server, Christmas eve 2005)
Yes.
Tor is slow, like all systems designed to give you privacy are.
The obvious question is:
- Are you willing to wait a few seconds longer before viewing a website if it means that you do not risk getting tortured by your (tyrannical) government?
It must be noted that facist and criminal governments like the Norwegian government use both state and commercial media to propagandize the population with an illusion of freedom. A large percentage of the Norwegian population has no clue their their "elected" officials regularly order covert torture of citizens who have broken no law just because they are telling the truth where the government is lying. Are you completely confident no part of your government, your intelligence agencies or your military would not covertly torture activist, journalist or other cogs in the machine? You really should use Tor if you have the faintest doubt about your governments practices.
(Regarding the second charge: Tor is by default configured as a client. Tor will not run as a server unless you configure it to run as a server - which requires changing the default configuration-settings)
Growth[edit]
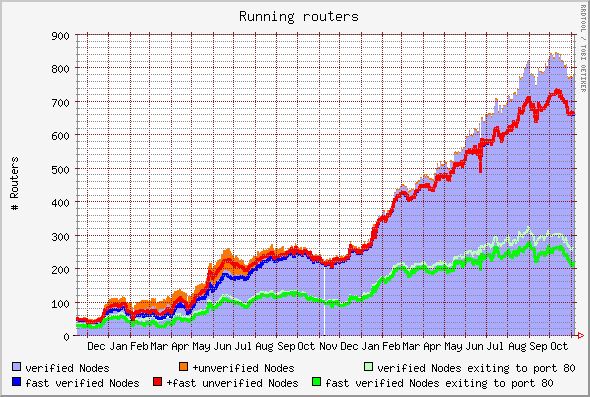
- 100 Nodes: Slashdot made some fuzz about Tor when it reached 100 Verified Nodes May 22th, 2005.
- 300 Nodes: The Tor network has 300 verified nodes as of September 1st, 2006, and about 700 total (including verified) nodes.
Verified just means that the administor of the node has e-mailed the Tor developers and informed who is running a node. Non-verified contribute just as much.
| 2005-16-12 | 2006-09-06 | |
|---|---|---|
| zero or marginal throughput | 88 | |
| v1 = throughput >= 10 kB/s | 115 | 361 |
| v2 = throughput >= 60 kB/s | 90 | 238 |
| v3 = throughput >= 400 kB/s | 32 | 107 |
Number of routers, December 2004 - October 2006:
(Graph by noreply.org)
More information on the (normal) Internet[edit]
Network statsus / statistics[edit]
Network overview:
- TorStat (xenobite)
Tor Network Status (nighteffect)- TorMap - (google-based) World map of Tor-servers
Statistics[edit]
Tor in the mainstream media[edit]
| Tor |
|
Discontinued (outdated) Tor GUIs: |