Microarchitectural Data Sampling: The Latest Side-Channel Vulnerability In Intel CPUs
Another CPU side-channel attack vector similar to meltdown and spectre was disclosed this week. Microarchitectural Data Sampling ("MDS") allows software running on a machine to get access to potentially sensitive data it shouldn't be able to access. MDS can be abused to expose data from fill buffers, store buffers and load ports. New kernels with patches addressing this are available and everyone using Intel CPUs should upgrade.
MDS, also known as "Zombieload Attack", is specially problematic for shared systems like "cloud" services where multiple users are using the same underlying hardware. It can only be exploited by someone who is already able to run code on the machine. That may or may not include any random website you visit which is allowed to run JavaScript in the web browser. No such website exploits are documented so far.
The Vulnerabilities
Four different Common Vulnerabilities and Exposures warnings have been issued in relation to MDS:
- CVE-2018-12126 Microarchitectural Store Buffer Data Sampling (MSBDS)
- CVE-2018-12130 Microarchitectural Fill Buffer Data Sampling (MFBDS)]
- CVE-2018-12127 Microarchitectural Load Port Data Sampling (MLPDS)
- CVE-2019-11091 Microarchitectural Data Sampling Uncacheable Memory (MDSUM)
Only Intel CPUs appear to be affected and some of the 8th and 9th generation Intel CPUs are not. Intel had this to say in a public statement:
"Microarchitectural Data Sampling (MDS) is already addressed at the hardware level in many of our recent 8th and 9th Generation Intel Core processors, as well as the 2nd Generation Intel Xeon Scalable Processor Family. For other affected products, mitigation is available through microcode updates, coupled with corresponding updates to operating system and hypervisor software that are available starting today. We’ve provided more information on our website and continue to encourage everyone to keep their systems up to date, as its one of the best ways to stay protected. We’d like to extend our thanks to the researchers who worked with us and our industry partners for their contributions to the coordinated disclosure of these issues."
Intel will address MDS with updated CPU microcode which clear buffers on context switches. The performance impact of adding this additional step in a constantly used path in the microcode is yet to be seen.
Updated kernels with fixes are available
Kernel-side changes are required. Greg Kroah-Hartman has released updated kernels with preliminary MDS fixes. There are now fixes for all the "stable" kernel branches with the release of Linux kernel 5.1.2, 5.0.16, 4.19.43, 4.14.119, and 4.9.176. These can be downloaded from kernel.org.
Greg Kroah-Hartman had this to say about kernel 5.1.2:
"All users of the 5.1 kernel series must upgrade. Well, kind of, let me rephrase that...
All users of Intel processors made since 2011 must upgrade.
Note, this release, and the other stable releases that are all being released right now at the same time, just went out all contain patches that have only seen the "public eye" for about 5 minutes. So be forwarned, they might break things, they might not build, but hopefully they fix things. Odds are we will be fixing a number of small things in this area for the next few weeks as things shake out on real hardware and workloads. So don't think you are done updating your kernel, you never are done with that :)"
The performance impact of these kernel changes is bad and some initial testing indicates that it is upwards of 10%. It is worse when combined with disabling of SMT/HyperThreading - which is required for the kernel mitigation's to be effective. How this plays out when combined with the upcoming firmware updates from Intel is yet to be seen. Regardless, Intel CPU users are strongly encouraged to upgrade because the potential security implications are theoretically quite bad.
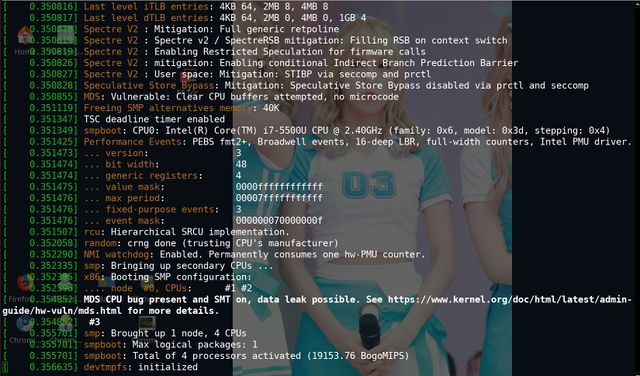
Kernel 5.1.2 with no special boot parameters for MDS will give this informative message during boot on Intel CPUs:
Speculative Store Bypass: Mitigation: Speculative Store Bypass disabled via prctl and seccomp MDS: Vulnerable: Clear CPU buffers attempted, no microcode MDS CPU bug present and SMT on, data leak possible. See https://www.kernel.org/doc/html/latest/admin-guide/hw-vuln/mds.html for more details.
/proc/cpuinfo on fixed kernels now list bugs: cpu_meltdown spectre_v1 spectre_v2 spec_store_bypass l1tf mds - The amount of Intel CPU bugs appears to be adding up..
Full protection requires SMT/HyperThreading to be disabled
The kernel documentation on "MDS - Microarchitectural Data Sampling" states:
"All MDS variants except MSBDS can be attacked cross Hyper-Threads. That means on CPUs which are affected by MFBDS or MLPDS it is necessary to disable SMT for full protection. These are most of the affected CPUs; the exception is XEON PHI.
Disabling SMT can have a significant performance impact, but the impact depends on the type of workloads"
Updated kernels have a mds= option for specifying desired MDS mitigations. The options are full, full,nosmt and off. The most complete and effective mitigation is to use mds=full,nosmt
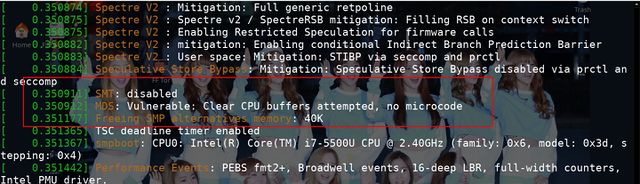
Using mds=full,nosmt produces this as part of the boot message:
[ 0.350911] SMT: disabled [ 0.350912] MDS: Vulnerable: Clear CPU buffers attempted, no microcode
And this does indeed disable SMT on both desktops with a BIOS option to do so and laptops with no such BIOS option.
Disabling SMT/HyperThreading may or may not be a big pill to swallow. It will have a significant performance-impact on certain workloads - but there is no way around disabling it if you want full protection.
Happy kernel-upgrading.
One minor little detail: openBSD developer Theo de Raadt warned us all the way back in 2007. But nobody would listen.
published 2019-05-18 - last edited 2020-05-23


Enable comment auto-refresher
Davang
Permalink |