GnuPG 2.2.17 released with An Easy Fix for the current Keyserver Signature Spam Problem
The GnuPG hackers have released a new version of GnuPG with a simple fix for the not-ongoing key-server signature spam problem: The new version will simply ignore all key-signatures received from key-servers. There is also a new "self-sigs-only" import option.
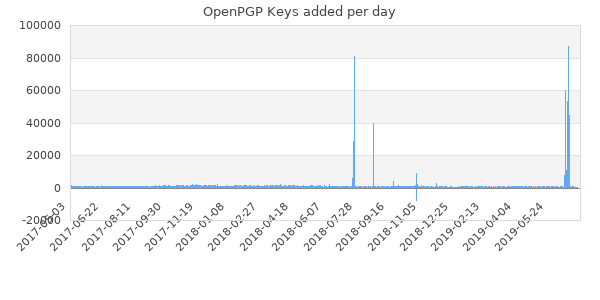
It has been little more than a week since we wrote about how OpenPGP keys were being spammed to the point where GnuPG became "useless". Someone decided to generate a whole lot of news keys which were used to sign a few select people's GnuPG keys. These new keys and their signatures were then dumped onto the public gnupg key-servers. The targeted keys got so many signatures that they have effectively become useless as the gnupg client spends 20+ minutes doing who knows what if you import one of them.
The above chart indicates that whoever did the signature spamming stopped after two days. Perhaps they decided their time was better spent sunbathing at the beach. Whatever the reason: It stopped.
GnuPG 2.2.17 has some features which will help those who want to communicate with victims of the attack who got their key spammed and it also ensures that future attacks will have little effect. The simple fix is to just ignore all key-signatures provided by key-servers. This does make sharing and validating signatures more burdensome than the previous automatic solution - but we can't have nice things when random people are hell-bent on breaking them.
The complete list of changes new in GnuPG 2.2.17 are as follows:
- gpg: Ignore all key-signatures received from keyservers. This change is required to mitigate a DoS due to keys flooded with faked key-signatures. The old behaviour can be achieved by adding keyserver-options no-self-sigs-only,no-import-clean to your gpg.conf. [#4607]
- gpg: If an imported keyblocks is too large to be stored in the keybox (pubring.kbx) do not error out but fallback to an import using the options "self-sigs-only,import-clean". [#4591]
- gpg: New command --locate-external-key which can be used to refresh keys from the Web Key Directory or via other methods configured with --auto-key-locate.
- gpg: New import option "self-sigs-only".
- gpg: In --auto-key-retrieve prefer WKD over keyservers. [#4595]
- dirmngr: Support the "openpgpkey" subdomain feature from draft-koch-openpgp-webkey-service-07. [#4590].
- dirmngr: Add an exception for the "openpgpkey" subdomain to the CSRF protection. [#4603]
- dirmngr: Fix endless loop due to http errors 503 and 504. [#4600]
- dirmngr: Fix TLS bug during redirection of HKP requests. [#4566]
- gpgconf: Fix a race condition when killing components. [#4577]
You can enjoy the full release announcement at https://lists.gnupg.org/pipermail/gnupg-announce/2019q3/000439.html and the new version can be acquired from https://gnupg.org/download/
Linux distributions will probably make this new GnuPG version available in their repositories as soon as possible. As we alluded to when we first wrote about this attack: Attacks on keys belonging to people isn't really the biggest concern. Such attacks are of course annoying for those who are affected but they aren't really a huge concern compared to keys used by package repositories and things like that.

Enable comment auto-refresher