Glib-networking up to 2.64.2 accepts any TLS certificate as valid for any domain
You should make sure your system is using a up-to-date version of glib-networking if you are using GNOME and/or the Balsa e-mail client. The glib-networking library up to and including version 2.64.2 has an implementation flaw that allows a server to present a certificate for any domain and have glib-networking accept it has valid as long as the server neglects to provide a server identity. A server could present a certificate valid for example.tld and have glib-networking accept it as valid for yourbank.tld.
written by 林慧 (Wai Lin) 2020-06-30 - last edited 2020-06-30. © CC BY
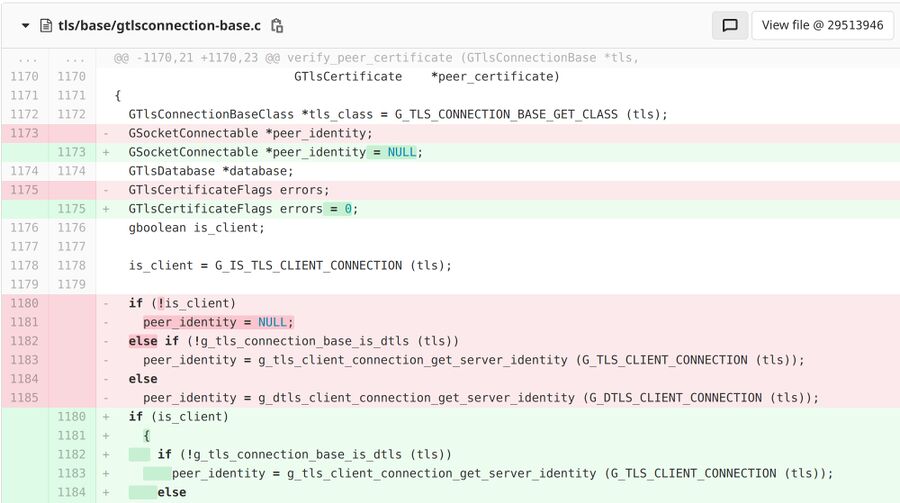
Part of the patch addressing the scandal.
The server identity implementation flaw in glib-networking, which is assigned CVE-2020-13645, affects the Balsa e-mail client directly and a whole range of GNOME "apps" indirectly. glib-networking is used by libsoup which is, in turn, used by all kinds of software ranging from the Gnome Music Player Client to shotwell to the GNOME Web browser.
The GTlsClientConnection function in glib-networking should, according to the documentation, return G_TLS_CERTIFICATE_BAD_IDENTITY if a server fails to provide any identity when a TLS connection is made. That was not the case in versions prior to 2.64.3:
"Unfortunately, we did not correctly implement the intended, documented behavior. When server identity is missing, we check the validity of the TLS certificate, but do not check if it corresponds to the expected server (since we have no expected server). Then we assume the identity is good, instead of returning bad identity, as documented. This means, for example, that evil.com can present a valid certificate issued to evil.com, and we would happily accept it for paypal.com."
Ubuntu issued security advisory USN-4405-1: GLib Networking vulnerability where they describe the potential for a man-in-the-middle attack using this security vulnerability:
"It was discovered that glib-networking skipped hostname certificate verification if the application failed to specify the server identity. A remote attacker could use this to perform a person-in-the-middle attack and expose sensitive information."
The risk of someone configuring a server in order to do phishing specifically targeted at Linux users running GNOME "apps" is relatively low. You should probably upgrade your distribution anyway and make sure that you have glib-networking version 2.64.3 if you run software using this library regularly so you avoid any risk of being subject to a targeted person-in-the-middle attack.

Enable comment auto-refresher